In today’s world, cyber-attacks are becoming more and more sophisticated, and businesses need to take proactive steps to protect themselves. One of the ways to do this is by using Attack Simulator in Office 365.
Attack Simulator is a tool in Office 365 that allows you to simulate various types of attacks, such as phishing and password spray attacks, and see how your employees respond. It can help you identify vulnerabilities in your security posture and take steps to address them.
Pre-requisite: Attack simulation training requires a Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2 license.
Membership/Roles required on tenant (Below)
- Global Administrator
- Security Administrator
- Attack Simulation Administrators: Create and manage all aspects of attack campaigns.
- Attack Payload Author: Create attack payloads that an admin can initiate later.
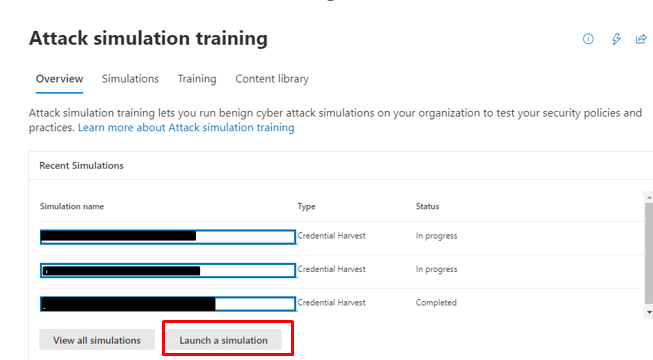
Simulations
Let’s jump into center implementation part.
in the admin centre from office 365 go to.
Microsoft 365 admin center > security > Attack simulator training.
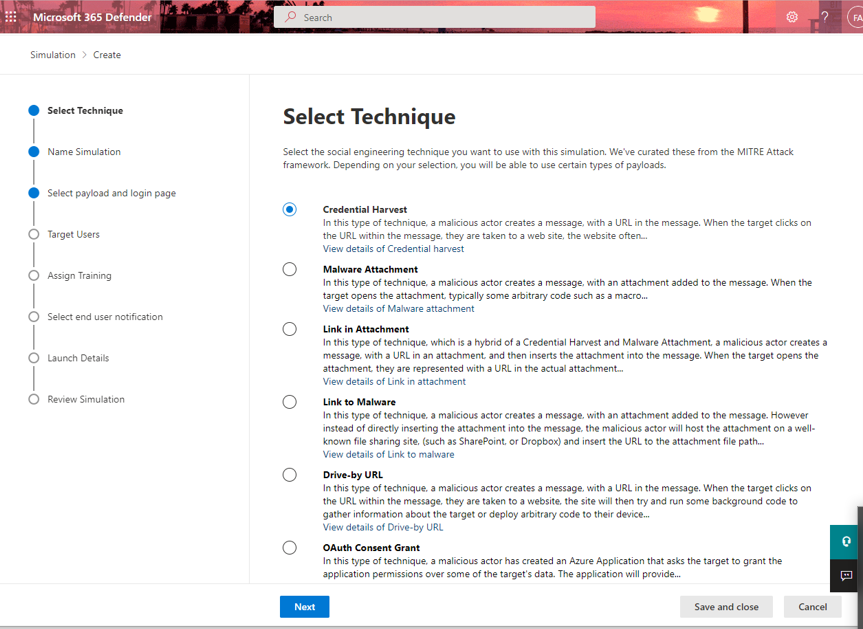
In Attack simulation training, multiple types of social engineering techniques are available:
- Credential Harvest: An attacker sends the recipient a message that contains a URL. When the recipient clicks on the URL, they’re taken to a website that typically shows a dialog box that asks the user for their username and password. Typically, the destination page is themed to represent a well-known website in order to build trust in the user.
- Malware Attachment: An attacker sends the recipient a message that contains an attachment. When the recipient opens the attachment, arbitrary code (for example, a macro) is run on the user’s device to help the attacker install additional code or further entrench themselves.
- Link in Attachment: This is a hybrid of a credential harvest. An attacker sends the recipient a message that contains a URL inside of an attachment. When the recipient opens the attachment and clicks on the URL, they’re taken to a website that typically shows a dialog box that asks the user for their username and password. Typically, the destination page is themed to represent a well-known website in order to build trust in the user.
- Link to Malware: An attacker sends the recipient a message that contains a link to an attachment on a well-known file sharing site (for example, SharePoint Online or Dropbox). When the recipient clicks on the URL, the attachment opens, and arbitrary code (for example, a macro) is run on the user’s device to help the attacker install additional code or further entrench themselves.
- Drive-by-url: An attacker sends the recipient a message that contains a URL. When the recipient clicks on the URL, they’re taken to a website that tries to run background code. This background code attempts to gather information about the recipient or deploy arbitrary code on their device. Typically, the destination website is a well-known website that has been compromised or a clone of a well-known website. Familiarity with the website helps convince the user that the link is safe to click. This technique is also known as a watering hole attack.
- OAuth Consent Grant: An attacker creates a malicious Azure Application that seeks to gain access to data. The application sends an email request that contains a URL. When the recipient clicks on the URL, the consent grant mechanism of the application asks for access to the data (for example, the user’s Inbox).
below you can specify the name and description and click next.

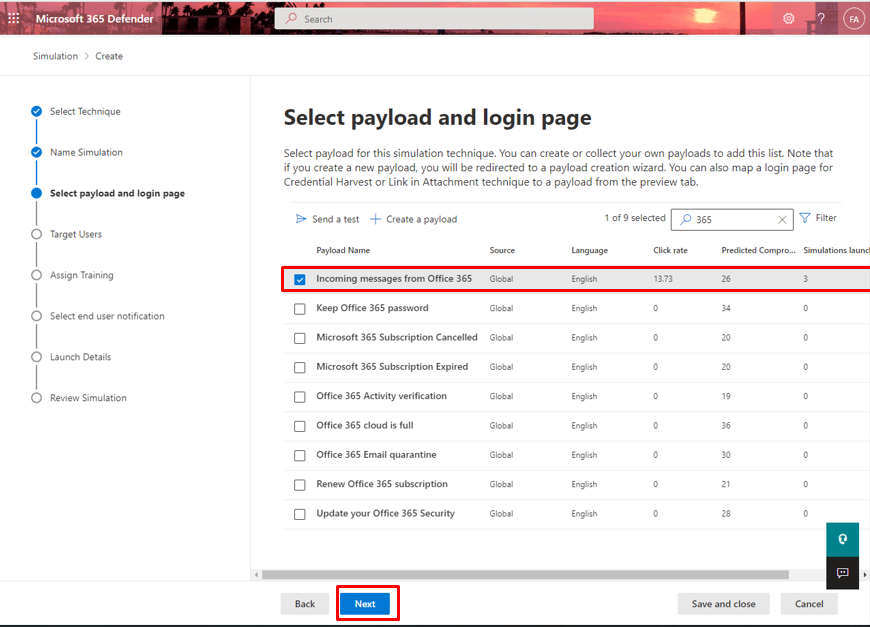
- Here you can select payload and login page, there are tons of payload available in different languages, I am selecting here *Incoming message from office 365*. And click next.
- Target users
- Include all users in my organization: to specify all the users on tenant.
- Include only specific users and group: you can also specify user and groups.
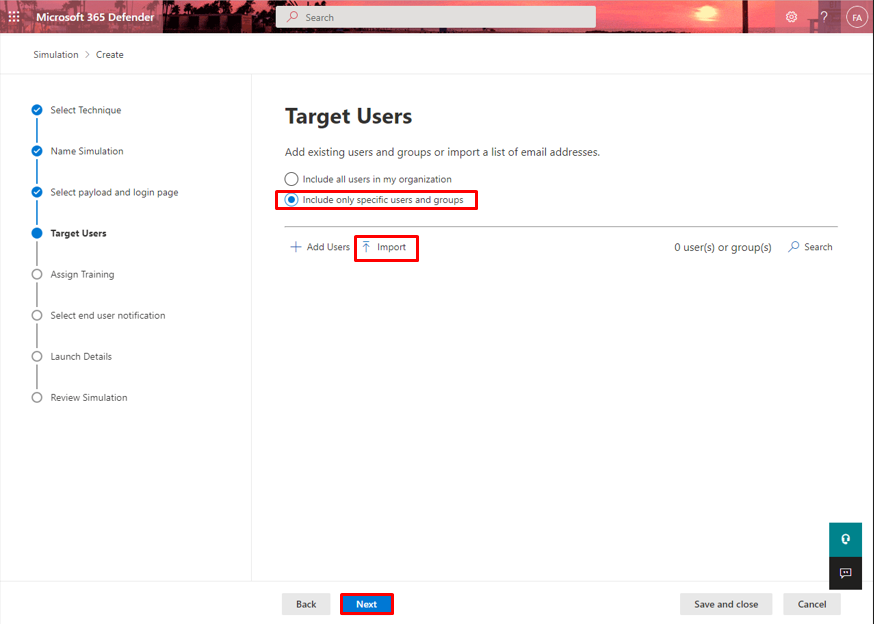
- Here I have specified import list of users in .csv format file as shown.

- Landing page, from below you can select Landing page preference and layout also you can edit layout. I have selected default.

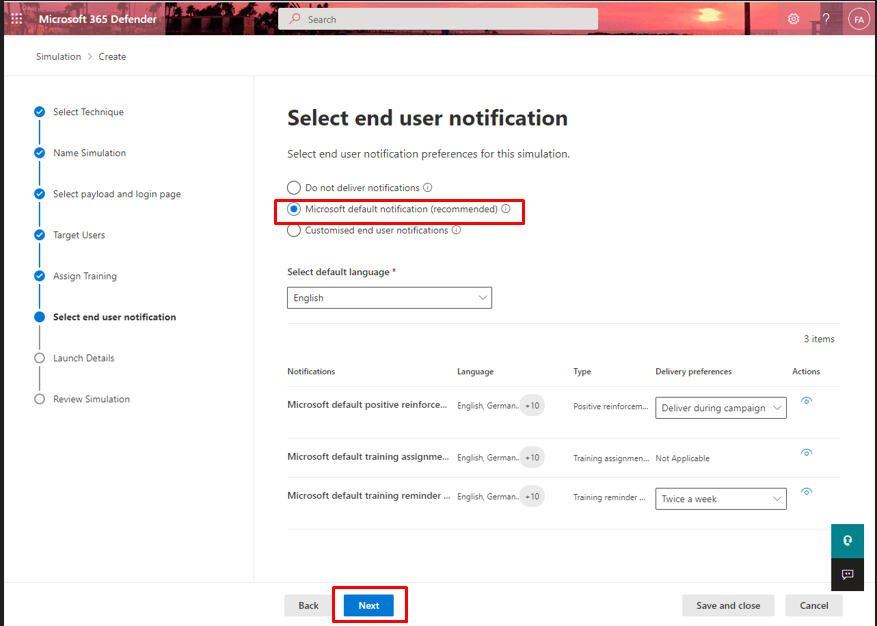
- Select end user notification. I am selecting Microsoft default notifications (Recommended)
- Launch details: configure when you want this simulation to launch.
- Launch these simulations as soon as I’m done.
- Schedule this simulation to be launched later. Here I am configuring for 7 days.

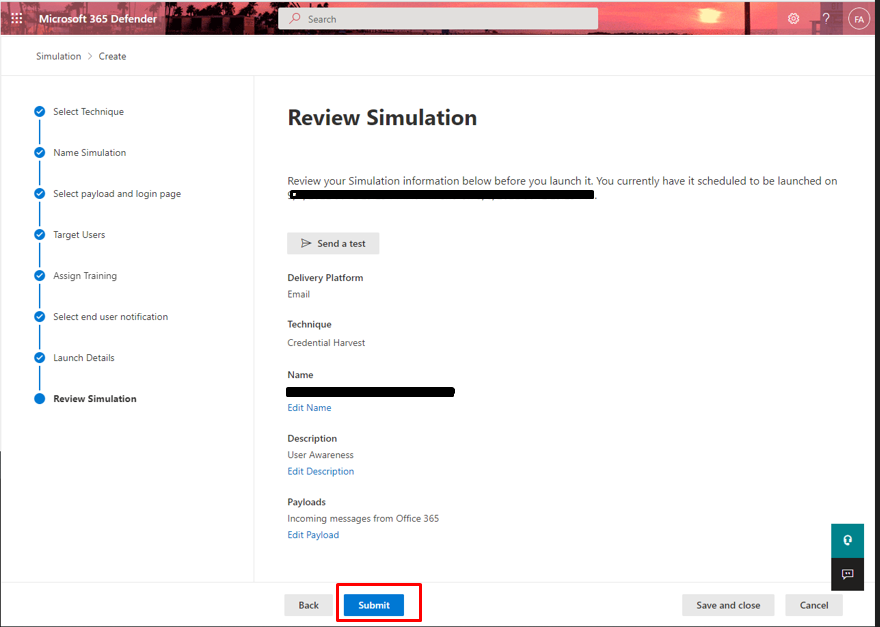
- Review simulation, once clicked next it will launch.

Here are some ways that Attack Simulator can improve your security posture:
- Identify vulnerable employees: Attack Simulator can help you identify employees who are more likely to fall for phishing emails or other types of attacks. By identifying these employees, you can provide them with additional training and resources to help them become more aware of the risks.
- Test your security controls: Attack Simulator can help you test your security controls and see how effective they are. For example, you can simulate a phishing attack and see if your email filtering system catches it. If it doesn’t, you can take steps to improve your filtering settings.
- Provide realistic training: Attack Simulator provides realistic training scenarios that mimic real-world attacks. This helps your employees understand the risks and how to avoid them in a more meaningful way than traditional training methods.
- Improve your incident response: By simulating attacks, you can improve your incident response plan and ensure that your team is prepared to respond quickly and effectively.
Conclusion:
In conclusion, mastering Office 365 security through Attack Simulator is an essential endeavor for safeguarding your digital workspace. By arming yourself with the knowledge and tools provided in this comprehensive guide, you can effectively fortify your organization’s defenses against potential cyber threats.