Chainsaw — designed as a “first-response” capability to identify threats within Windows event logs quickly.
Chainsaw offers a “generic and fast method of searching through event logs for keywords, and by identifying threats using built-in detection logic and via support for Sigma detection rules” — written in Rust and accessible via the command line.
Chainsaw’s Authors Describe It As:
- Search and extract event log records using event IDs, string matching, and regex patterns.
- Hunt for threats using Sigma detection rules and custom built-in detection logic.
- Output in ASCII table, CSV, or JSON formats.
- Document tagging (detection logic matching)
Chainsaw includes the ability to search through event logs by event ID, keyword, and regex patterns; extraction and parsing of Windows Defender, F-Secure, Sophos, and Kaspersky AV alerts; detect key event logs being cleared or the event log service being stopped; users being created or added to sensitive user groups; brute-force of local user accounts; RDP logins, network logins, etc., and Sigma rule detection against a wide variety of Windows event IDs. Security folks can get Chainsaw for free.
Steps to use Chainsaw:
- Install Chainsaw in your system.
- Once the application installs, then you have to open CMD as administrator.

- I have tested one command for this task as below:
- Command: 20-01-2023-Nikunj-laptop-WindowsLogs.txt
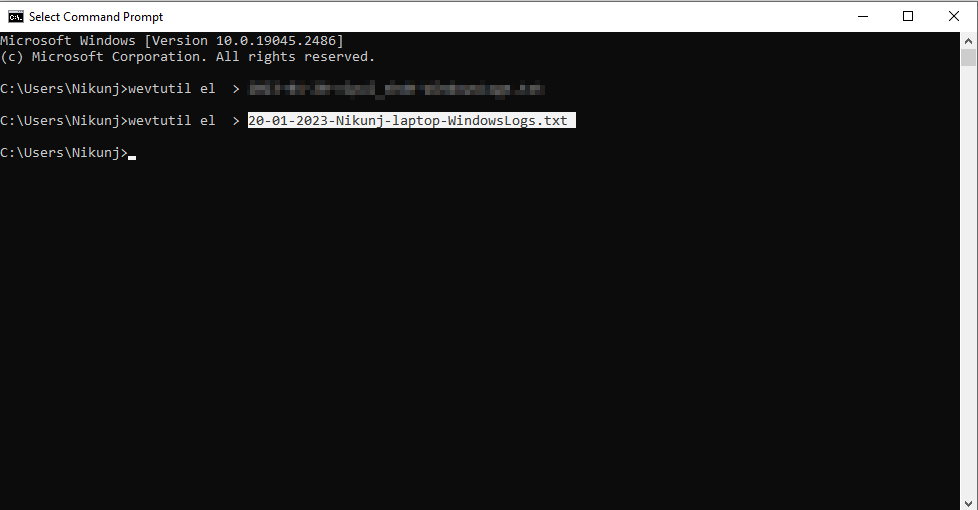
- Output: System generates one txt file in my system (Windows log file)

- There are many more commands and things you can do with this tool.