Cybersecurity—a term that has been increasingly doing the rounds over the past few years—has evolved to keep pace with the rise of new and sophisticated attacks. While most IT Managed Service Providers (MSPs) excel in IT infrastructure management, there’s an important question to ask: are we placing equal emphasis on cybersecurity? This gap demands attention because cybersecurity is not just about IT anymore; it is a necessity that has transcended it to be a part of business resilience and growth strategy. This blog discusses the increasing demand for cybersecurity services and how it has become inevitable and can benefit if you transition from an MSP to a Managed Security Services Provider (MSSP).
Contents
1. The increasing demand for cybersecurity in 2025
- Why the Demand is Growing
- Addressing the Challenge
2. Services you can provide
3. Risks involved if cybersecurity is not prioritized
4. To hire cybersecurity experts or to outsource them?
- Simulation Training
5. Is outsourcing a feasible option?
6. Conclusion
The increasing demand for cybersecurity in 2025
Clients know it. Clients want it. They are seeking MSPs that have a cybersecurity edge and expertise. For MSPs, who provide managed IT solutions this represents both a challenge and an opportunity: are you merely following traditional security best practices, or are you prepared to address the broader, rapidly evolving scope of cybersecurity?
1. Why the Demand is Growing
The surge in demand is being driven by multiple factors. One key element is the explosion of advanced technologies like artificial intelligence (AI). While AI offers significant benefits, its misuse poses serious risks. Poorly managed AI systems can become sources of data leakage or other vulnerabilities.
Moreover, cybercriminals are leveraging generative AI and advanced large language models to create cyberattacks. For instance, these tools can generate phishing content, social engineering scripts, and even write malicious codes. Studies have revealed that generative AI tools can produce exploit code with alarming accuracy when provided with detailed descriptions. This lowers the barrier to entry for cybercrime, enabling even non-technical actors to execute attacks simply by inputting the right prompts into AI chatbots.
2. Addressing the Challenge
Based on a research done by Enterprise Strategy Group, stronger cyber security tools and procedures topped the list of the year’s most significant IT initiatives by a significant margin (27%) followed by the use of AI and machine learning (16%) and data analytics for real-time business intelligence and customer insight (14%).
“Cybersecurity is not the whole and sole responsibility of an MSP. The client has to be equally cautious and aware”
MSPs must educate their clients about these risks, implementing proactive defences such as AI-based threat detection, endpoint protection, and ongoing security and simulation training for employees. For end-users, even one careless action—such as clicking a malicious link—can have devastating consequences.
As we are into 2025, cyber risks are endless which is why the demand for MSSPs or MSPs that provide advanced security solutions would be on the rise.
Services you can provide
Some IT Managed Service Providers are already offering services that resemble those of a without fully realizing it. If you already provide services such as IT infrastructure deployment and maintenance, storage configuration, or network management as an MSP, transitioning to an MSSP can be a natural extension.
However, traditional MSPs looking to make the leap to becoming an MSSP will need to undergo a more significant transformation. This includes hiring skilled security analysts or cybersecurity consultants, establishing Security Operations Centers (SOCs), and investing in advanced technologies for real-time monitoring and threat detection across clients’ IT infrastructures.
To achieve this, you will need to build your MSSP capabilities from scratch, which involves several critical steps:
- Invest in the right Tools: Acquire advanced cybersecurity tools that support threat detection, vulnerability management, and real-time monitoring. Implement security automation tools to streamline threat detection, response, and compliance reporting, improving efficiency and accuracy.
- Hire Experts: Onboard security professionals such as security analysts, threat hunters, and incident response experts with the right skill sets.
- Establish SOC: Build an in-house or outsourced SOC to monitor and manage your clients’ security environments continuously.
- Revise procedures and protocols: Update internal processes to prioritize cybersecurity and align them with best practices like those outlined in frameworks such as ISO 27001.
- Develop Incident Response Plans: Create and test incident response protocols to ensure you are prepared to address security breaches effectively.
Risks involved if cybersecurity is not prioritized
When sensitive data falls into the wrong hands, the consequences for MSPs and their clients can be catastrophic. Identity theft, financial fraud, and even significant legal repercussions often follow such breaches. For MSPs, the risks of neglecting cybersecurity services go beyond individual incidents—they strike at the core of their business model and client relationships.
Prioritizing data privacy and adhering to stringent regulations such as GDPR, CCPA, and ISO standards require MSPs to adopt robust policies that govern data collection, storage, and usage.
This involves implementing-
- Advanced cybersecurity tools
- Detailed documentation practices
- Conducting employee training programs
Without these, businesses run the danger of long-term reputational damage, which can be more difficult to recover from, than fines.
Moreover, MSPs need to extend cybersecurity awareness to their clients. Even a seemingly harmless action, such as a user clicking on a phishing link, can lead to severe consequences. For example, a single ransomware attack could compromise the personal and financial data of thousands, opening the door to lawsuits from affected clients claiming negligence.
The implications of a data breach extend far beyond immediate recovery costs. A significant breach can result in business interruptions, lost revenue, and costly lawsuits, especially when sensitive client data is compromised. Which is why transitioning to an MSSP or having advanced cybersecurity offerings becomes an indispensable element.
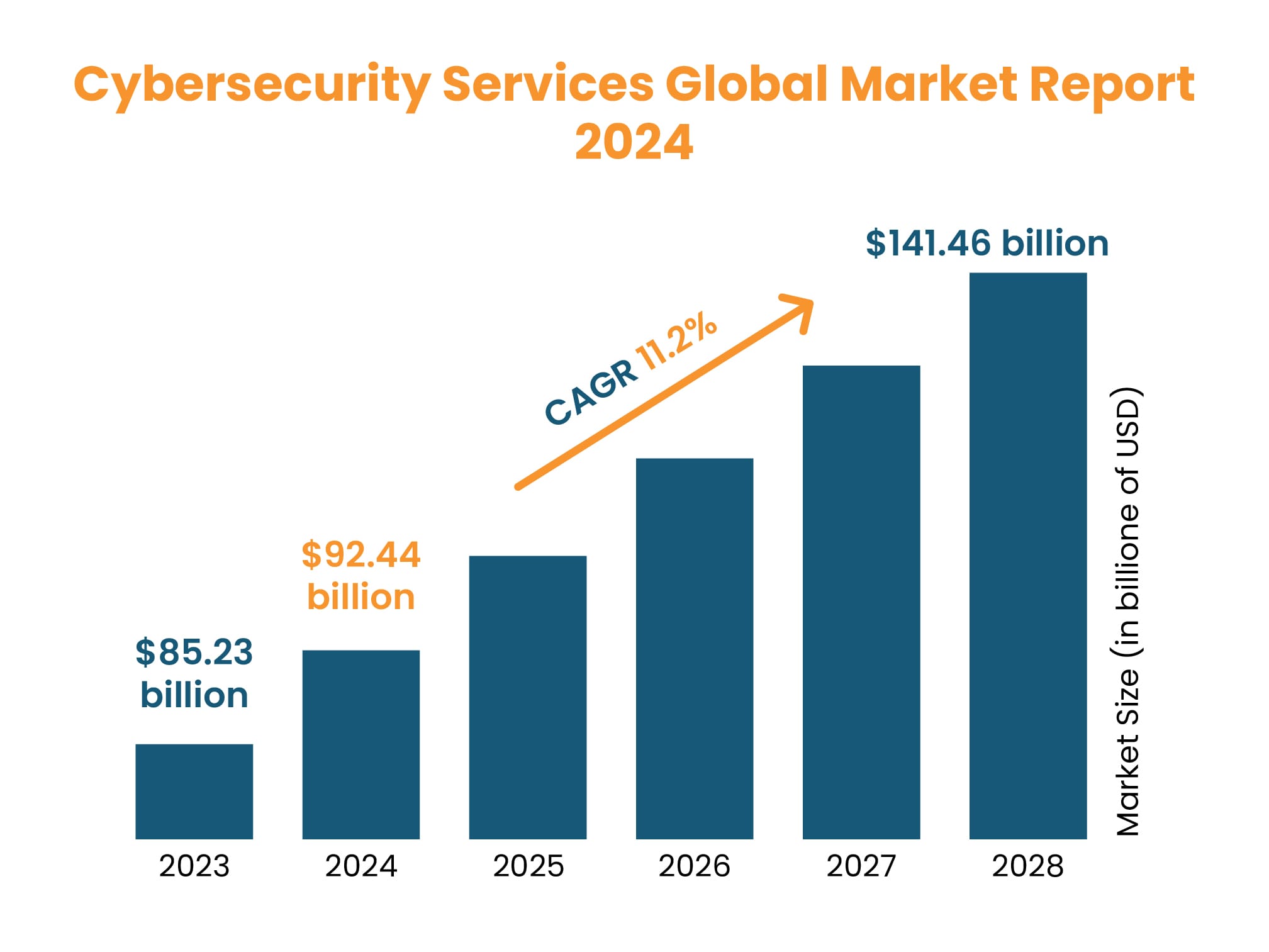
[Image Courtesy:The Business Research Company]
To hire cybersecurity experts or to outsource them?
Transitioning to an MSSP would mean building a specialized security team with in-depth knowledge and expertise on threat intelligence, vulnerability management, and incident response best practices. This expertise would empower you to provide not just outsourced managed IT Services but more comprehensive and effective security services to your clients.
- Experts can identify vulnerabilities and stall risks, reducing the likelihood of cyberattacks
- Invest in the necessary security technologies, such as Security Information and Event Management (SIEM) and Endpoint Detection and Threat Response (EDR) platforms. Consider partnering with vendors to access advanced security solutions and expertise
- Cybersecurity experts assist clients in meeting industry regulations and standards helping you avoid legal penalties
Simulation Training
An added service or training you can provide to your clients is Simulations. They help mimic real-world threats such as ransomware and phishing, but in a controlled environment. By incorporating cybersecurity simulation training, organizations foster a proactive approach to security, ensuring their teams are well-prepared for cyber threats.
Simulations would help you monitor client responses to realistic scenarios, identify gaps in their defence, and tailor future training to address these weaknesses effectively. Your cyber team and end clients both would gain a thorough understanding of attack vectors which would help improve the overall cybersecurity posture.
Is outsourcing a feasible option?
One of the simplest ways to provide managed security services is by partnering with an established MSSP or Master MSPs who have a cybersecurity edge. These providers specialize exclusively in security, eliminating the need for you to invest in building, operating, and maintaining a SOC or implementing a SIEM solution.
When selecting an MSSP, it’s important to choose a partner that aligns with your business processes and existing technology. Avoid MSSPs that require you to overhaul your operations or replace current technologies. Instead, consider outsourcing to those offering flexible, customizable managed IT solutions that seamlessly integrate with your organization’s offerings and functions.
Conclusion
In today’s rapidly evolving threat landscape, it is imperative for MSPs to transition into MSSPs to act as the proactive line of defence for their clients. Clients depend on their IT partners not just for network uptime but for proactive protection against ever-growing cyber threats. By evolving into MSSPs, MSPs position themselves as trusted allies, offering comprehensive security solutions that go beyond reactive support. One thing to understand is- It doesn’t have to be intimidating, but it does require awareness and action to shield ourselves from external threats.
If you have narrowed in in the option of outsourcing, reach out us at Infrassist and we’d be happy to know your requirements to tailor a solution that helps expand your security offerings and safeguard clients’ network.