How does AD Authentication with Firewall
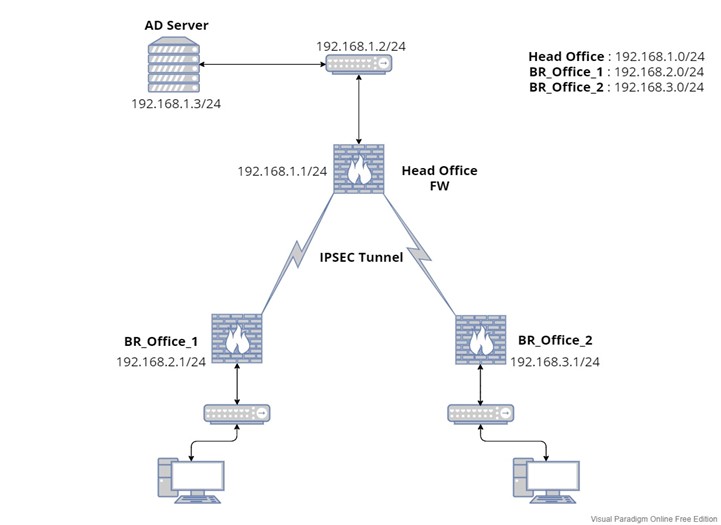
One of our end customers wanted an AD Authentication to be done between its Head Office and Branch Office.
They had Sophos Firewall installed and wanted a secure connection in the entire network.
In this blog, we demonstrate how you can add an authentication server on Sophos Firewall for robust security and how to import AD groups.
Here’s an overview of our process-
- Refer to IP address as per the diagram
- After Basic parameters configuration into the firewall, we need to create IPSEC tunnel between Head Office and Branch Office.
- First, we need to create IPsec Tunnel between Head Office and BR_Office 1 & BR_Office 2.
- Configure the Authentication server on all Firewall and
- Install STAS into the Head Office AD server
IPsec Tunnel Configuration
Head Office Firewall Configuration
Step 1:
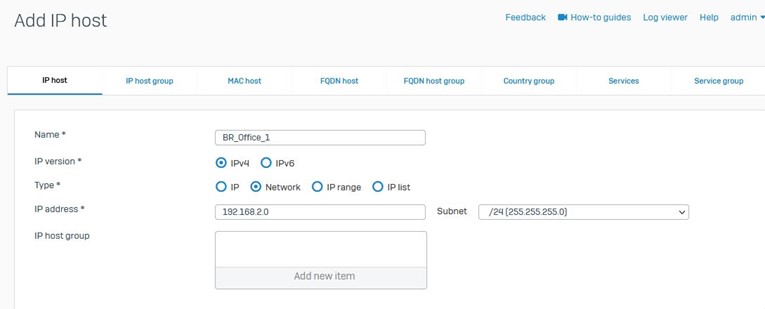
Host Creation
In your Sophos Panel, go to System >> Host and Services >> IP Host
In our case, as shown below we have created hosts for each the Head Office and the 2 branch offices.


Step 2:
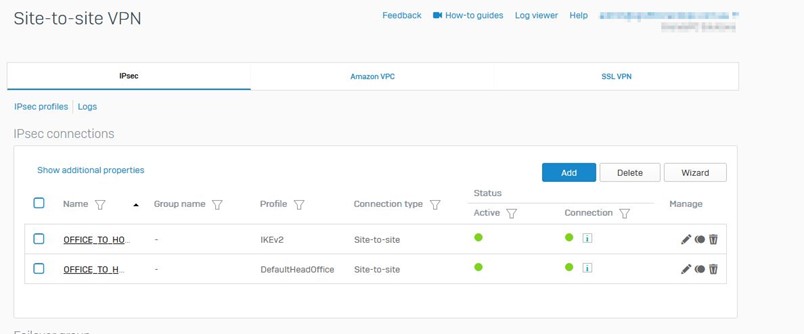
Add IPSEC connection:
Configuration >> site-to-site VPN >> IPse

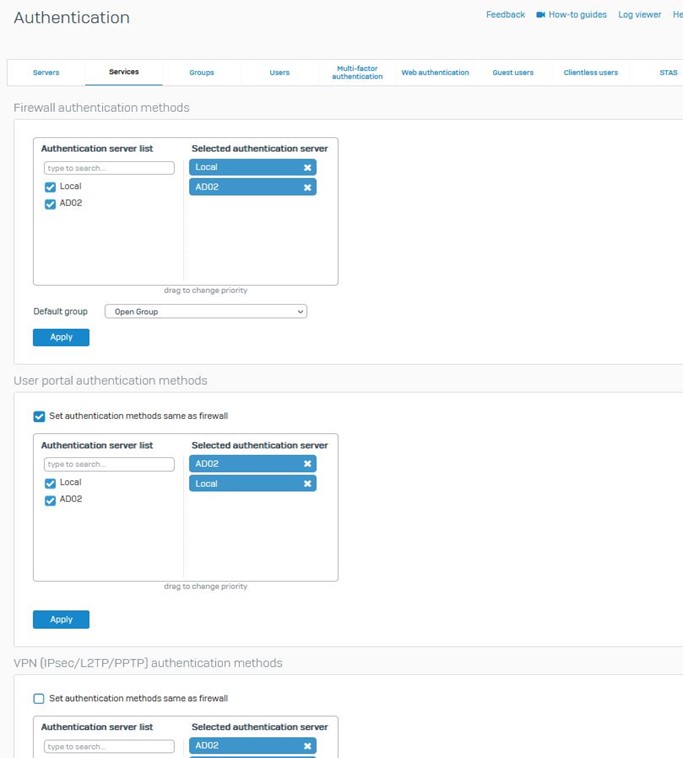
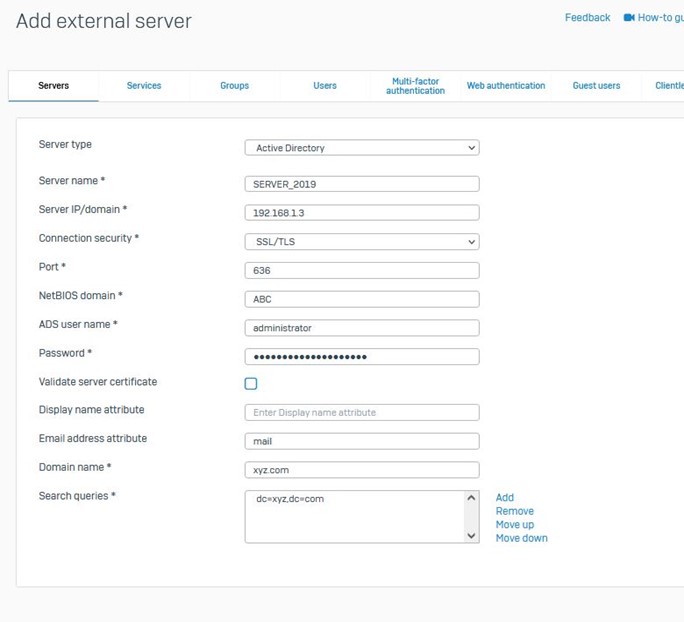
Step 3: Configure AD Server in firewall:
Under Configure, go to “Authentication” > Servers > Add
Select Server Type as “Active Directory”.
In the Connection Security option, make sure you either select SSL/TLS or START/TLS (as they are both secure)
Fill in the rest of the details and then click on the “Test Connection” button at the bottom to check the connectivity and then click on Save if everything is okay.
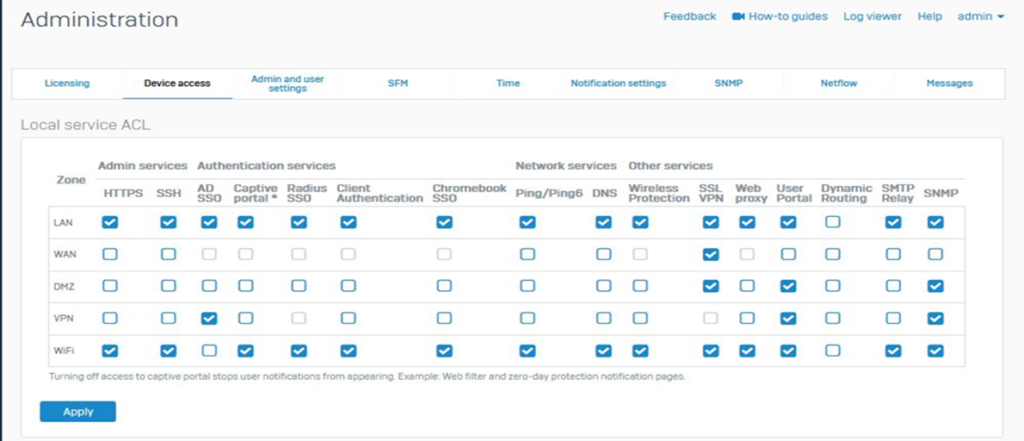
Before enabling STAS, you need to enable AD Authentication Service:
To do that, go to Adminstration > Device Access > Check necessary requirements and click on Apply
Once done, Go to Authentication > Services and choose your AD server as the primary authentication method before integrating STAS.
What is STAS?
Stands for Sophos Transparent Authentication Suite. By keeping track of domain controller events, Sophos STAS authentication can match authenticated users with their corresponding IP addresses. Once the user’s identity is known, the Sophos UTM can provide access based on that user.
How does Authentication work?
STAS tracks events taking place in the Domain Controller (DC). Each DC is supposed to track user log-ins and log-outs.
DC Collects these events and forwards them to the STAS Collector, the information collected is consolidated and forwarded to Sophos UTM along with the IP address and username.
The UTM pushes the Active Directory to establish which group the user falls under and then it allows or denies access based on permissions granted.
Integrate STAS:
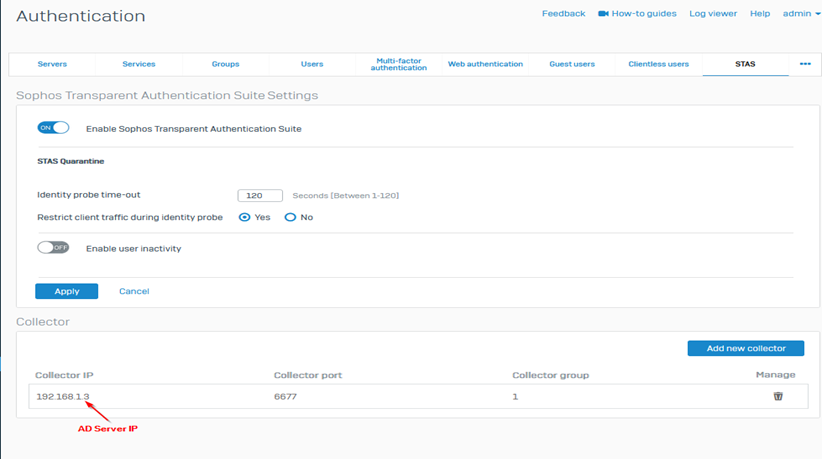
- On the firewall, go to Authentication > STAS.
- Toggle On the Enable Sophos Transparent Authentication Suite and click Apply
- Click on Add new collector, specify your settings and then click Save
Add Firewall Rule:

STAT Configuration on AD Server:
- Download STAS Client from Firewall.
Configuration>>Authentication>>Client Download
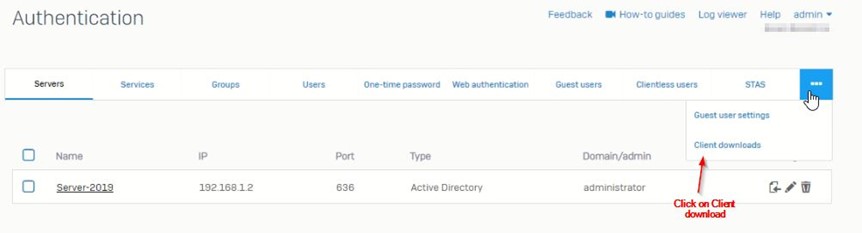
Download it on Server Device

Install Client into AD server.

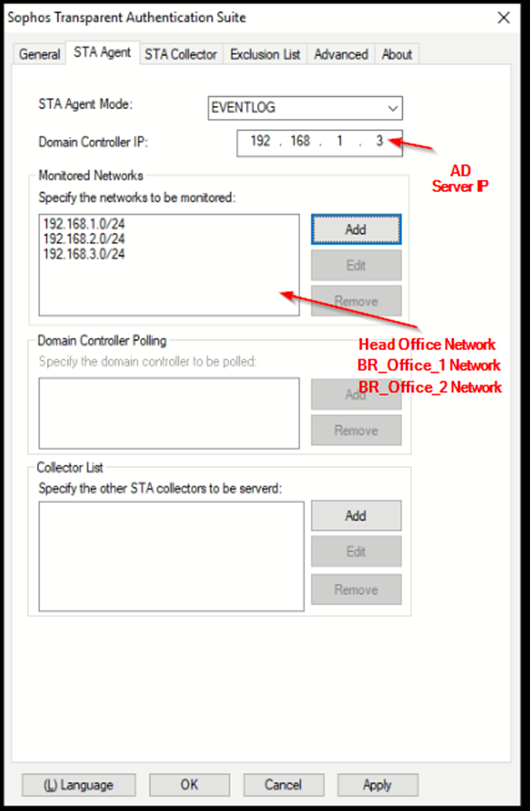
STAT Agent Configuration:
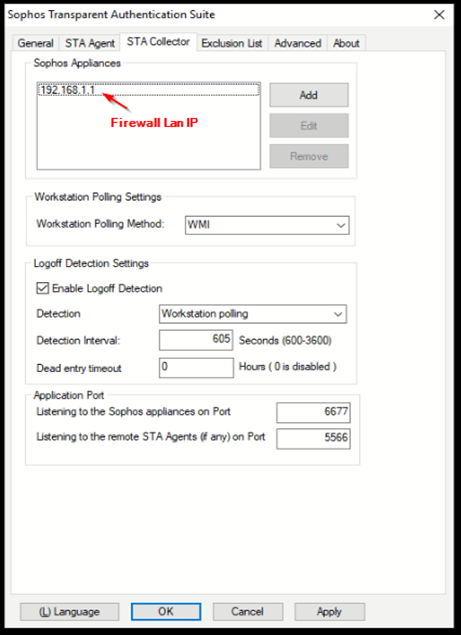
STAT Collector Configuration:
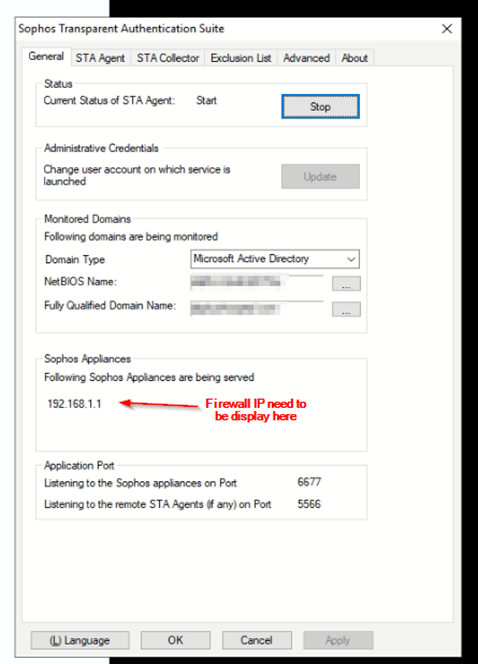
How to check if the STAS Service is Running or not
In order to check that, you need to start WMI Service in AD Server
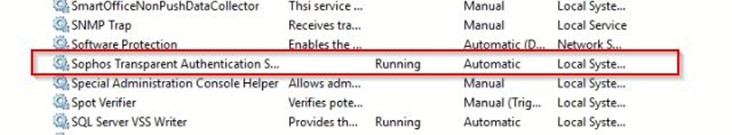
Start WMI Service in AD Server:


Installed AD Certificate to Avoid SSL/TLS error:
It can happen to you that you get an SSL TLS Error when you try to work the above mentioned procedure. To avoid that, do the following:
Go t o AD Console>> Manage>> Add Roles and Features
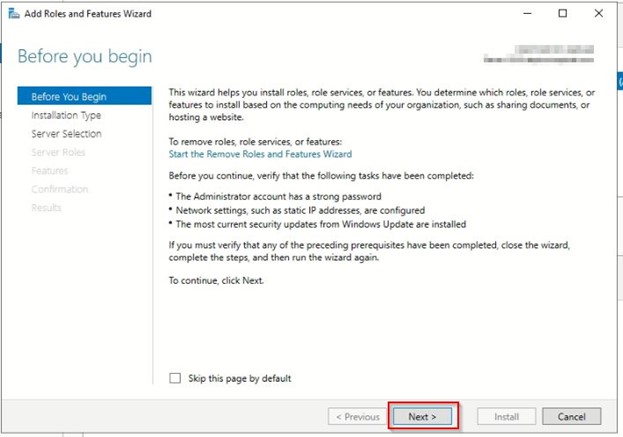
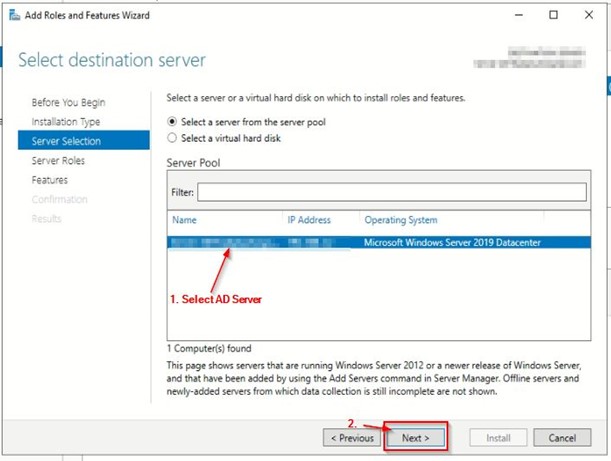
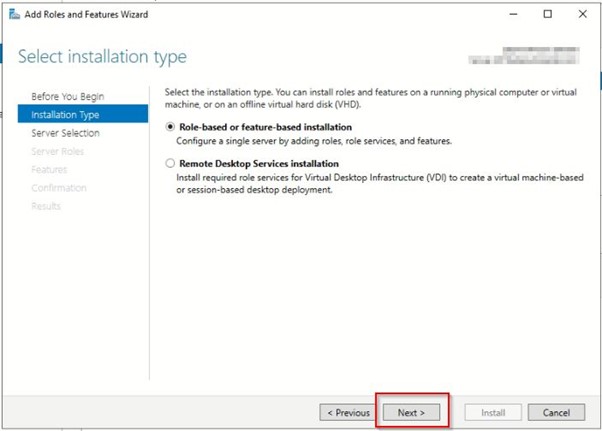
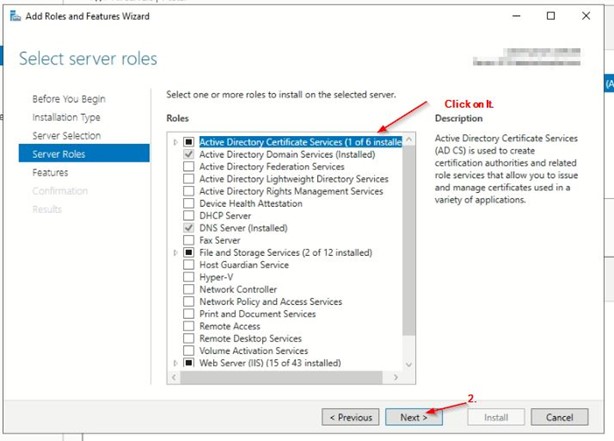

Check Server Roles and check the status.
Now follow the IPSec Configuration step for the Branch offices as well and you are good to go.
Take a look at our firewall audit checklist to measure the effectiveness of your firewall setup.